Are you using Splunk as a SIEM and concerned about NIST CVE-2024-3094? Well then this post is for you! So lets get right to how we detect CVE-2024-3094 associated with xz-lib version 5.6.0 and 5.6.1
… but first! If you are new to Splunk, then consider taking our fundamentals course. You can click the image/link below within the next 2 minutes to get access to an EXCLUSIVE training course discount…

Description of CVE-2024-3094:
Malicious code was discovered in the upstream tarballs of xz, starting with version 5.6.0. Through a series of complex obfuscations, the liblzma build process extracts a prebuilt object file from a disguised test file existing in the source code, which is then used to modify specific functions in the liblzma code. This results in a modified liblzma library that can be used by any software linked against this library, intercepting and modifying the data interaction with this library.
Detection Steps with Splunk® Enterprise
The detection of CVE-2024-3094 with Splunk® Enterprise is a simple 3 step process that involves making sure you have the prerequisites, deploying additional inputs.conf settings (if needed), and then writing a search that detects the vulnerable versions. If you’re ready to begin, then lets get started with step 1.
Step 1: Prerequisites:
a. Splunk® Universal Forwarder w/Splunk_TA_nix installed
b. “Package.sh” should be enabled similar to the example below
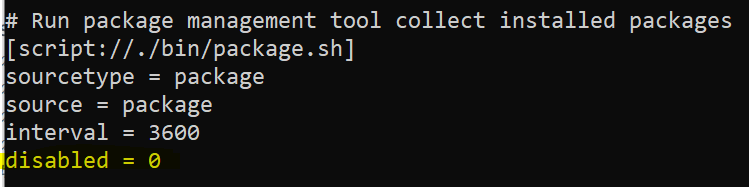
Note: that the UF needs to be restarted to enable the input if it was previously started without the input.
Step 2: Deploy the updated inputs / app
If you need to deploy the app out, you’ll only need to deploy it to Linux hosts. Do make sure you enable splunkd restart on your app deployment
Step 3. Detect the CVE
Now allow time for the data to arrive at your indexing tier and you should be able to run this search as a detection
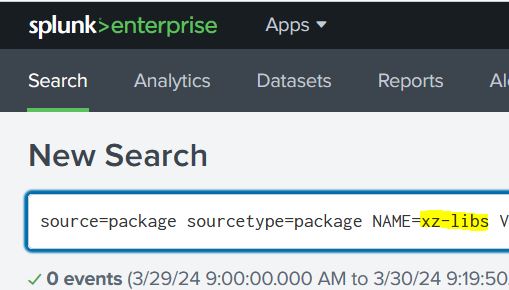
source=package sourcetype=package NAME=xz-libs VERSION IN ("5.6.0","5.6.1")Note: You may need to add index=os or index=Your_Linux_TA_Data_Index_here, but by default the data will be in index=main
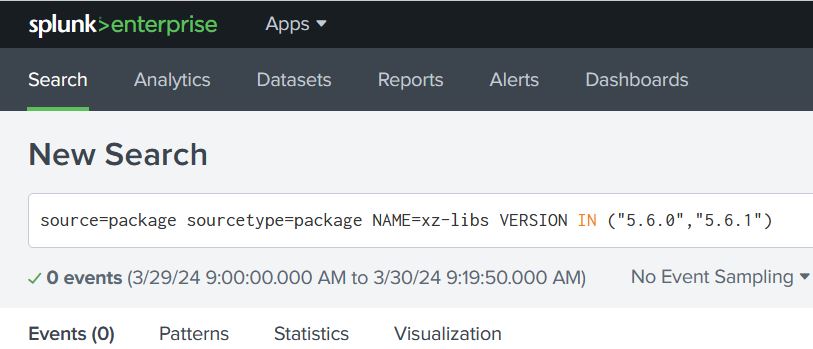
You’ll probably want to take the search a few steps further. First thing that comes to our mind is adding a “| stats latest(_time) as latest_time by host”. When you manipulate _time like that you’ll notice it converts to epoch, so you’ll probably want to convert it back to human readable format with “| convert ctime(latest_time)”. The full search might look something like this:
source=package sourcetype=package NAME=xz-libs VERSION IN ("5.6.0","5.6.1")
| stats latest(_time) as latest_time by host
| convert ctime(latest_time)Conclusion
In conclusion, detecting CVE-2024-3094 associated with xz-lib versions 5.6.0 and 5.6.1 with Splunk® Enterprise is vital for maintaining the security integrity of your systems. By following the straightforward detection steps outlined above, Splunk users can proactively identify and mitigate the risks posed by this vulnerability. Through the implementation of these measures, organizations can bolster their cybersecurity posture and safeguard against potential exploits targeting this particular CVE.
Additional Tips
- Continuous Monitoring: Establishing continuous monitoring practices within your Splunk environment ensures ongoing detection of potential threats and vulnerabilities, including emerging CVEs such as CVE-2024-3094. Regularly review and refine your detection mechanisms to adapt to evolving security landscapes.
- Threat Intelligence Integration: Integrate threat intelligence feeds into your Splunk instance to enhance the accuracy and effectiveness of your detection capabilities. Leverage threat intelligence platforms to stay informed about emerging threats and vulnerabilities, enabling proactive response and mitigation strategies.
- Patch Management: Implement a robust patch management process to promptly address known vulnerabilities in software components such as xz-lib. Regularly update systems with vendor-released patches and security updates to mitigate the risk of exploitation and ensure the resilience of your infrastructure.
- Collaboration and Knowledge Sharing: Foster collaboration among security teams, system administrators, and Splunk users to share insights, best practices, and mitigation strategies related to CVE-2024-3094 and other security threats. Establishing a culture of knowledge sharing promotes collective defense against cyber threats and strengthens organizational resilience.
- Threat Hunting: Embrace proactive threat hunting initiatives within your Splunk environment to identify potential indicators of compromise (IOCs) associated with CVE-2024-3094. Leverage Splunk’s search capabilities and analytics tools to conduct thorough investigations and uncover suspicious activities or anomalies indicative of exploitation attempts.
By incorporating these additional tips into your cybersecurity practices, you can further enhance your organization’s ability to detect, prevent, and respond to security threats effectively. Stay vigilant, stay informed, and stay secure with Splunk® Enterprise.
As always, if you want to learn more about detecting this vulnerability or resolving the issues created by the vulnerability, then please reach out to our team and we’ll be happy to help!